TRM Labs says North Korean IT staff have laundered tens of millions in USDC and USDT whereas secretly working for blockchain startups.
North Korea continues to depend on crypto to quietly fund its weapons applications and the U.S. authorities is stepping up efforts to close it down. On July 8, the U.S. Treasury’s Workplace of Overseas Belongings Management sanctioned a North Korean hacker, Track Kum Hyok, who they are saying helped arrange a widespread scheme involving pretend distant staff at unsuspecting tech and crypto firms.
In accordance with a latest report from blockchain forensic agency TRM Labs, Track was linked to Andariel, a cybercrime unit that’s a part of North Korea’s navy intelligence. They defined that he performed a key position in inserting IT staff — most of whom have been really North Korean operatives — into jobs at U.S. firms through the use of stolen American identities and pretend paperwork.
Many of those jobs have been in web3, crypto infrastructure, or blockchain-related software program improvement.
TRM Labs stated these staff operated from international locations like China and Russia whereas pretending to be U.S.-based freelancers. They received paid in stablecoins similar to USD Coin (USDC) and Tether (USDT). From there, the cash appeared to have flowed by layers of wallets, mixers, and conversion companies earlier than ending up within the fingers of the North Korean regime.
“Treasury stays dedicated to utilizing all accessible instruments to disrupt the Kim regime’s efforts to avoid sanctions by its digital asset theft, tried impersonation of Individuals, and malicious cyber-attacks.”
Deputy Secretary of the Treasury, Michael Faulkender
Analysts at TRM Labs identified that that is simply the newest signal that North Korea’s Reconnaissance Common Bureau — the identical company behind Lazarus and Bluenoroff — continues to be utilizing cyber ways to help navy objectives. Treasury officers, they famous, have been warning that crypto theft and id fraud stay central to North Korea’s technique for avoiding financial strain.
The analysts defined that the scheme uncovered by OFAC depends closely on pretend personas. Track was allegedly liable for constructing these pretend identities, utilizing stolen knowledge from actual U.S. residents. As soon as employed, North Korean operatives might have labored for months and even years in U.S. firms below false names.
Additionally they famous that OFAC sanctioned 4 firms and one different individual linked to a Russia-based community that allegedly helped handle these pretend IT jobs. These companies reportedly signed long-term contracts with DPRK-linked corporations and have been conscious they have been coping with North Korean staff.
Most of the staff focused jobs within the crypto sector particularly, the place funds have been simpler to anonymize. As soon as the crypto was obtained, TRM Labs analysts stated, it was unfold throughout a number of wallets and finally transformed into fiat utilizing OTC brokers, a few of whom have been beforehand sanctioned.
Cyber alliance
The most recent OFAC’s motion adopted a sequence of coordinated strikes by U.S. businesses, together with the Division of Justice and the FBI. On June 5, 2025, the DOJ additionally filed a civil forfeiture criticism searching for to grab over $7.7 million in crypto, NFTs, and different digital belongings believed to be linked to the identical North Korean community.
TRM Labs says the employees used identities like “Joshua Palmer” and “Alex Hong” to get employed at crypto startups and different tech corporations. They have been paid in stablecoins, with proceeds routed by centralized exchanges, self-hosted wallets, after which on to higher-level regime figures like Kim Sang Man and Sim Hyon Sop, each already below U.S. sanctions.
The DOJ’s investigation, in accordance with analysts, revealed that elements of the operation relied on infrastructure based mostly in Russia and the UAE. Investigators discovered the usage of native IP addresses and cast documentation, which helped the North Korean staff disguise their true identities. This, they stated, underscored simply how worldwide the scheme had grow to be.
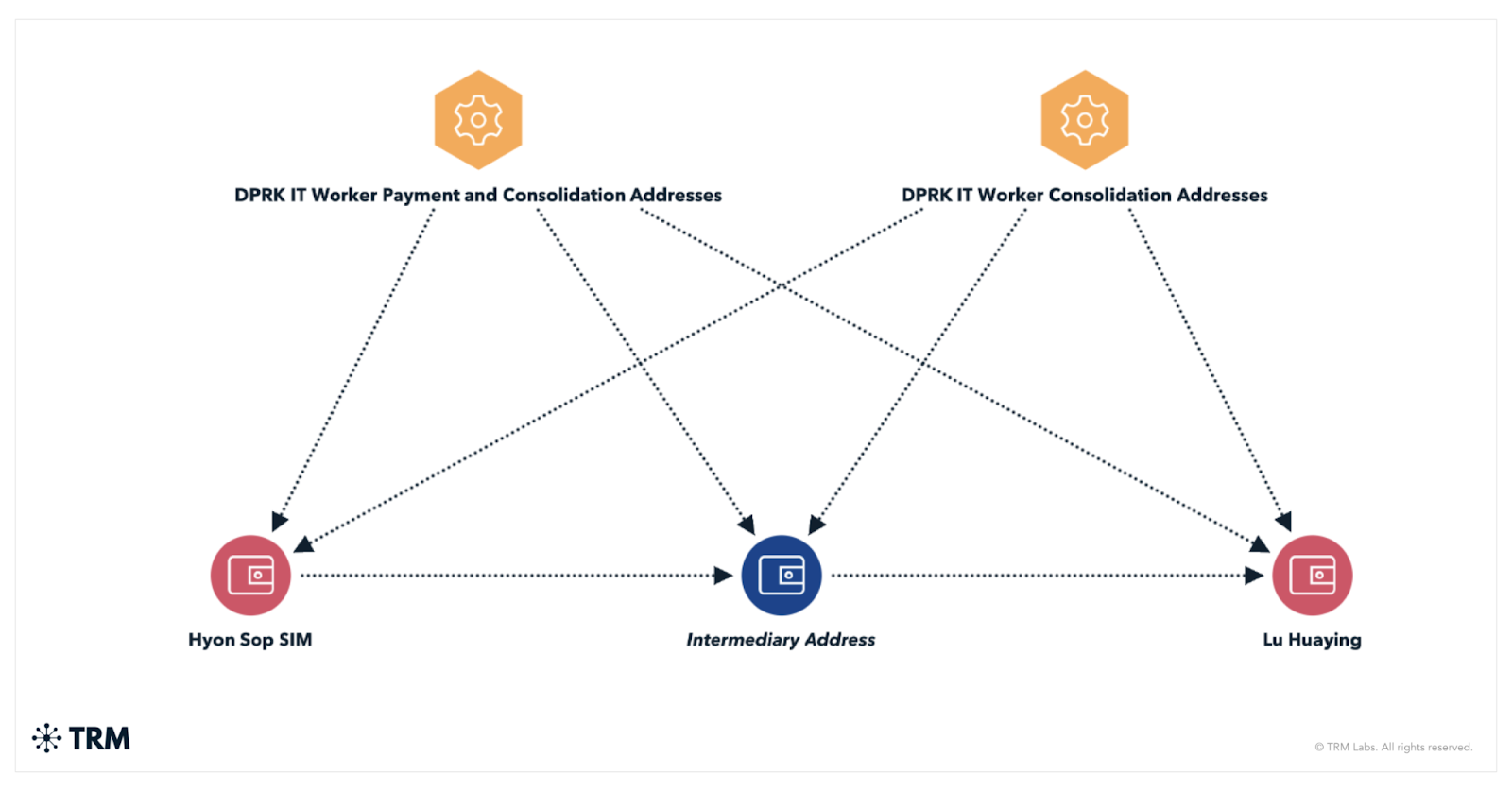
Blockchain knowledge reviewed by TRM confirmed that after funds reached mid-level wallets, the cash was break up into smaller parts, routed by privacy-enhancing instruments, and finally exchanged for fiat through OTC desks. A type of OTC brokers had already been sanctioned by OFAC in late 2024.
As for legislation enforcement efforts, the FBI and different businesses efficiently seized a portion of the laundered digital belongings, together with USDC, ETH, and a few high-value NFTs. The analysts described these seizures as a part of a broader laundering technique meant to interrupt up the cash path and make detection far tougher.
TRM Labs says the U.S. authorities’s newest motion sends a message that crypto stays a high-risk channel for sanctions evasion, particularly in terms of North Korean operations. The blockchain intel agency warned that firms hiring distant builders — particularly within the blockchain house — must take further care in verifying who they’re actually coping with.







